The world of mobile connectivity is rapidly evolving, with eSIM, iSIM and to some extent SoftSIM reshaping how cellular modules and devices connect to networks. While all three technologies promise software-defined flexibility and innovation, they differ fundamentally in how they achieve security and scalability.
In this blog, we explore these differences, clarify key concepts like Trusted Execution Environment (TEE) vs. Secure Element (SE), and explain why GSMA and carriers (or mobile network operators, MNOs) continue to favour more secure, hardware-based solutions. That preference is essential for long term supportability and interoperability.
The Security Foundations: Trusted Execution Environment (TEE) vs. Secure Element (SE)
When discussing SIM technology, it’s essential to understand the security layers that underpin it:
Trusted Execution Environment (TEE)
A TEE is a secure area within a device’s main processor that isolates sensitive operations, such as cryptographic functions or key management. While it offers protection from software-based attacks, its integration with the main processor makes it more exposed to potential vulnerabilities, such as advanced malware or side-channel attacks.
Secure Element (SE)
An SE is a standalone hardware chip designed exclusively for security. It operates independently of the device’s main processor, making it inherently resistant to physical tampering and software breaches.
Analogy
Think of a TEE as a secure room within a house, while an SE is a dedicated vault separate from the house itself. While both offer protection, the SE is purpose-built for resilience against a wider range of attacks.

What People Usually Mean when they ask about “SoftSIM”
In our experience, when people ask about “SoftSIM,” they are usually just seeking a software-defined solution—a concept that eSIM and iSIM already deliver through the Remote SIM Provisioning (RSP) standards defined by the GSMA (SGP.02, SGP.22, and SGP.32). These standards allow for:
- Dynamic Carrier Switching: The ability to remotely provision, update, or replace SIM profiles without physical intervention.
- Simplified Supply Chains: Eliminating the need for physical SIM cards reduces manufacturing, distribution, and deployment complexities.
eSIM and iSIM deliver these benefits while also complying with hardware-based security requirements for unmatched security.
SoftSIM vs. eSIM and iSIM: The Key Differences
SoftSIM
SoftSIM replaces the physical SIM with a software-only solution, storing network keys and profiles in the device’s main processor or cellular module.
Capabilities:
- Eliminates the SIM component from the Bill of Materials (BoM)
- Savings made on cost, space and power consumption
- Implements alternative secure storage and processes for key installation
Challenges:
- Despite secure methodologies, SoftSIM’s reliance on software limits trust. Without a hardware Secure Element, network keys are more vulnerable to tampering or theft.
- The GSMA and carriers remain reluctant to adopt SoftSIM due to its inability to meet their stringent hardware-based security standards. Consequently, availability of carrier profiles will be limited
- Any cost, space and power saving benefits are often very marginal and can be matched by eSIM or iSIM.
eSIM and iSIM: Software-Defined, Hardware-Secured
eSIM and iSIM deliver the same software-defined, cost, space and power benefits that SoftSIM promises but within the framework of hardware-based security.
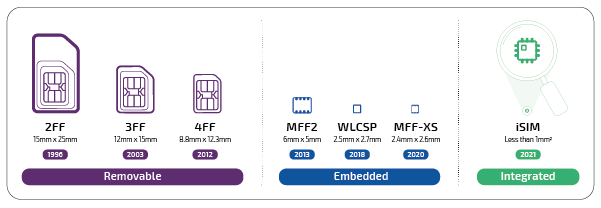
- eSIM: A standalone hardware chip which can be mounted as a discrete component on the PCB or integrated into cellular module chip package. The latter approach has cost, space and power benefits. Both support RSP standards, enabling remote provisioning and flexible carrier switching.
- iSIM: An evolution of eSIM that integrates the Secure Element directly into the device’s processor, maintaining hardware security while reducing physical space requirements.
It’s important to note that all SIM formats – removable, embedded and integrated – can be deployed as software-defined eSIM or iSIM solutions. Download our Remote SIM Provisioning Guide for a breakdown of terminology, functionality and benefits.
Why GSMA and Carriers Favour Hardware-Based Solutions
Hardware Immutability
eSIM and iSIM store network keys in tamper-proof Secure Elements, offering unparalleled protection against physical and digital attacks. This assurance cannot be matched by SoftSIM, which relies on the less secure Trusted Execution Environment.
Standards and Trust
The GSMA mandates stringent standards (SGP.02, SGP.22, SGP.32) to ensure global interoperability and security. Hardware Secure Elements meet these requirements, fostering trust among carriers and enabling seamless connectivity across networks.
Carrier Confidence
Carriers are particularly sensitive about the security of their network keys, as these are critical to authenticating devices. Solutions without hardware security, like SoftSIM, face significant resistance from carriers due to security risks.
eSIM, SIM, and iSIM production and data generation follow strict GSMA regulations, much like the stringent standards in the credit card industry. Only certified sites can handle sensitive data, with rigorous audits ensuring secure processes and compliance.
By contrast, SoftSIM data generation lacks these enforced standards, leaving security practices inconsistent and less reliable. The GSMA’s tightly controlled environment ensures that eSIM and iSIM credentials are managed with the highest trust and integrity, similar to how payment credentials are safeguarded in certified facilities. This distinction highlights why hardware-secured solutions remain the gold standard for mobile connectivity.
Ultimately, SoftSIM is more vulnerable to attacks like key extraction, tampering, and unauthorized provisioning. For Enterprise IoT users, this poses significant risks, including network breaches, data theft, ransomware and service disruptions. This is just like someone having your credit card details (including the 3-digit security code) and being free to use it online, only the scale of the problem in IoT is drastically bigger and more dangerous.

Without hardware-backed protection, compromised SoftSIM environments could jeopardize sensitive industrial systems and critical IoT applications at scale.
- Energy/Utilities: Grid disruptions, blackouts, manipulated distribution, billing, infrastructure failures.
- Healthcare: Stolen data, disrupted devices, compromised equipment, endangered patient care.
- EV Charging: Disabled chargers, fraud, stolen credentials, disrupted transportation, logistics impacted.
- Smart Cities: Traffic gridlock, surveillance breaches, utility failures, emergency system disruptions.
SIM-based authentication is part of the first line of defence in IoT Security. Our IoT Security Framework is built around three pillars DEFEND, DETECT and REACT. Read more about other measures including Anomaly & Threat Detection here.

Why eSIM is the Best Solution Until iSIM Becomes More Mainstream
While iSIM represents the future of mobile connectivity, eSIM is currently the most accessible and simplest to deploy . Its widespread adoption, hardware-based security, and compliance with GSMA standards make it the most practical and secure choice for cellular modules today.
Proven and Trusted Technology
eSIM has established itself as a reliable technology supported by carriers and GSMA. It provides a hardware Secure Element for storing network keys, ensuring robust protection against tampering and cyber threats.
Global Support and Ecosystem
eSIM is already integrated into a broad range of devices and cellular modules, from smartphones to IoT systems. The existing infrastructure around eSIM, including GSMA’s Remote SIM Provisioning (RSP) standards, ensures compatibility and support across networks worldwide.
Software-Defined Flexibility
Like iSIM, eSIM enables software-defined connectivity, allowing users to switch carriers or provision profiles remotely without needing a physical SIM card. This capability delivers convenience and adaptability for modern applications.
Bridge to the Future
While iSIM holds the promise of even greater integration and efficiency, eSIM serves as a proven stepping stone, combining the benefits of hardware security with software-defined flexibility. It provides a secure, scalable solution that meets today’s connectivity needs while paving the way for mainstream iSIM adoption which is currently only economical for very high volume quantities.
Conclusion: eSIM Today, iSIM Tomorrow
eSIM is the best option for cellular modules in the current landscape. It delivers software-defined convenience with the security of hardware, addressing the key concerns of GSMA and carriers. However, as iSIM becomes more mainstream, its advantages—greater integration, reduced physical footprint, and the same hardware-backed security—will make it the optimal choice for the future.
For now, eSIM remains the practical and secure solution for bridging today’s connectivity demands and tomorrow’s innovations. As the ecosystem evolves, iSIM will undoubtedly take the lead, offering the next generation of seamless, secure, and scalable mobile connectivity.
For more information download our Single SIM for Global Deployments and IoT Security Framework guides.